With the increasing spread of information and technology today, the advantages of networking have become essential. With the competitive market and the enormous amount of data to be analyzed,
The Benefits of Creating a Network or Its Needs
Bob used to say that someone who is unfamiliar with English and lacks computer skills is practically illiterate. There is a subtle point to this. That the two are not an advantage, but a necessity. So it is better to think about the necessity of networking rather than the benefits .
The exchange of information is increasing day by day
One of the benefits of networking is getting into the information world. Today, information technology has become an indispensable part of any business, whether business or service, and has forced corporate executives to network. Businesses and companies that want to take advantage of the day-to-day system will need to network their collection information anyway.
Nowadays, studies and experiences of specialists and managers have shown that the right use of technology is a success and a benefit for the company.
The benefits of networking are provided only by a dedicated network support team that can optimally use the system.

Organizations associated with up-to-date technology place great importance on member networking and statistical analysis.
The benefits of networking to the fullest extent
To summarize the benefits of networking in a few words: command, trust, security, and smooth, easy transactions. Network support ensures the correct operation of these exchanges, monitoring software and hardware bugs, detecting viruses and threats online and taking action against them, as well as staying up to date.
The benefits of networking are the potential that can be activate as much as possible.
Generally speaking, networking and support networking is a great approach to achieving new business strategies. The door to your business is always open to customers.
This provides significant business opportunities and is one of the advantages of network services . Network support is a reminder of this communication set, as well as any possible defects that may occur in the network.
Managers can design short- and long-term strategies using information analytics. You can actually use the perspective that network support provides.
Network support in this regard can inform managers about issues that will play a vital role in their business development.
Network support ensures fault-free operation of network infrastructure and tools. Informs the manager of the latest technologies in their business. So another advantage of networking is providing managerial approaches to corporate executives.

One of the benefits of creating a network is connecting to a huge amount of information
Let’s see the two sides of the coin
In today’s competitive market, up-to-date technologies play a key role. This is just one side of the coin. How this network is set up and what experts manage and manage it depends on the quality of the network support company in which the complex operates.
A professional network support team can dramatically reduce costs with the expertise, knowledge and skills of an expert and enable the benefits of network services . They keep themselves updated with technology to provide opportunities for executives.
Obtaining classified information and analyzing it can be effective in increasing production rates over a short period of time. The approaches that emerge also alert managers to the transition from enterprise to larger and larger scale organizations.
This is what every manager can accomplish. Managers think of three things: maintaining, updating, and developing a business that is more likely to be accessed through a professional network support team. On the other side of creating a network , there are some problems that may arise. This is where the role of the backup team becomes clear.

Network backing designs information nodes to optimally connect the set
Pre-treatment of the benefits of networking
One of the benefits of networking is identifying infrastructure weaknesses. The manager grapples with issues before they reach critical points. Real-time reports and network history are categorized statistically, providing a perspective for the manager to design new approaches to sustain and develop.
Benefits of networking services are usually provide by outsourcing or outsourcing a company to a company rather than hiring multiple rows in the company. The IT unit focuses on its work and is fully responsible for network monitoring. In this case, a larger group with more expertise and experience guarantees network support.
Control large scale sets
Network support is even more important when the set that is network is larger. The more developed an organization or business is, and the larger the so-called large-scale, the presence of an up-to-date expert team in network support. In fact, this is one of the benefits of creating a large-scale collection control network .
Large-scale connections require specialized support
The job of engineers and network managers is to provide IT services: Monitoring, optimizing, securing and optimizing effective and efficient networking to meet customer needs. The wider the information network, the more difficult and sophisticated the monitoring will be. This does not mean, of course, that smaller networks do not need network support; especially if the computer is network, engineers in this area will save time and money.
To get the most out of the benefits of networking in our suite, we need an expert and responsible support team. With over a decade of experience in the field, Ryan’s backup team is ready to launch and support the network with its dedicated team of experts.
High-speed Internet access significantly speeds up the process. The question most users ask is how to convert mobile Internet to WiFi so other devices can use it. In this article, we will look at different ways to convert mobile Internet to WiFi.
Most people’s SIM cards support 4G or 4.5G internet, and some operators offer speeds close to the above, though in some cases you can see 4G at the top, but when opening pages or downloading files, It is not fast and in some cases does not exceed several hundred kb. However, operators such as First Mobile and Irancell have good coverage and often provide high Internet speeds. This has led some mobile Internet users to replace the fixed Internet.
Convert SIM card internet to WiFi by making Hotspot WiFi
One of the simplest ways to transfer your phone’s Internet to other smart devices is to activate the Hotspot feature. In this way, the phone appears as a router and the Internet sends the phone to other devices covered. The above method is the simplest solution available to the user to transfer the Internet to the phone. All you have to do is turn on the Mobile Hotspot feature.
When you turn on the feature, the smartphone will provide you with a network name and password that will enter the phone’s Internet dongle or laptop settings by entering this information. The above feature has the advantage of allowing you to put the phone in the place where it receives the best signal.
The higher the phone is, the closer it gets to the windows,
it receives good communication signals from the masts and offers high speed internet.
However, the aforementioned method has two major drawbacks: first, the phone gets too hot, which causes serious problems in the hot summer season, and secondly, the battery runs out quickly. For this reason it is best not to use the above method on your main phone and use a cheap one.

The second solution is to convert SIM card Internet to WiFi through MiFi dongles
The second method, which works better and does not cause problems for your phone, works on MiFi dongles. MiFi dongles are removable flash-like devices that allow you to plug in a SIM card and convert your SIM card to Wi-Fi internet.
These MiFi dongles are popularly known as Mobile WiFi. These dongles are divided into two main groups. The first group only supports certain SIM and Internet operators.
The second group is not limited to specific operators and can be used by different operators. When buying the above dongles you should be careful:
The first thing to note is the support capability.
First, check if the dongle you are trying to buy is supported by different operators. If you are only limited to one particular operator.
Most MIF dongles do not need to be configured and installed on specific software. All you have to do is connect the SIM card to the dongle to turn the SIM card into a WiFi network.
When purchasing, make sure that the dongle supports 4G LTE Internet. Some MyFace dongles are limited to 3G, which bring speed limitations and are cheaper than 4G LTE.
Some of these dongles use specific mobile applications that provide user details. No doubt buying dongles that support proprietary software is better than those without proprietary software.

The third solution is to use 3G / 4G modem ports
Some of the modems on the market are equipped with USB ports capable of supporting 3G / 4G. Some of the USB dongles available on the market for the SIM card Internet are not capable of converting the Internet of Things SIM to WiFi because they only send the Internet to a device that is connected via a USB port to Troubleshooting If your router’s modem supports USB 3g / 4G connectivity,
you can simply plug the USB dongle into the modem and then convert the Internet SIM card to a WiFi network. In this case, all smart devices will be able to receive a SIM card network.
When you connect a dongle to a modem, all you have to do is go to the router settings
and the 3g / 4G Setting section and configure the parameters associated with the SIM card internet.
As you can see, there are effective ways to transfer SIM card Internet to other equipment. No doubt dongle-based solutions work better than smartphones because they receive their energy from the device they are connected to, and secondly, they do not cause premature damage to the phone and its battery.
]]>Establishing home wireless network security is a great step to prevent any intrusion, from using your bandwidth to stealing information.
But what is a home wireless network? Simply put, home wireless networking means connecting an Internet access point (Access Point) to a router. This connection is generally made with cable. The goal is to quickly and easily connect multiple devices to the network.
Often after the wireless router is set up, we find it somewhere in the house and forget about it! As long as all the devices are connected to the wireless network, nothing matters. It is true? No!
Internet router is one of the most important devices in our home. You may not have realized this yet. The router is our gateway to the Internet. It’s also the gateway to our privacy for cybercriminals! They can access our Internet-connected devices and access all available information.
Don’t forget this tip! We are living in an era of information leaks, blackmail attacks (a bunch of malware that demands ransom restrictions) and other online threats. So, we have to worry about the security of our home network. The steps needed to increase home network security are numerous.
Why is Home Wireless Network Security Important?
The only security action most people take is to set a password for their network. The purpose is to prevent unwanted neighbors and other people from accessing your network. But we need to be more serious about securing our home network than creating a password . One of the serious dangers is the low security of your network and access by online criminals . They can hear your transit traffic and gain important information. They can also exploit your network to launch malicious attacks. Attacks like the middle man attack or information theft.
For this reason, it is wise to learn how to secure your home wireless network against cybercriminals. The Internet of Things (connecting all home devices to the internet and being remotely controlled by mobile phones, etc.) is getting wider day by day. With all the Internet-connected devices you have, securing your home network is even more important. This may seem daunting, but it is necessary.
In this article, you’ll learn how to provide more security for your home network. This will make your information less vulnerable.

Use the steps outlined above to increase the security of your home wireless network:
Step 3: Change the default name for your home network
If you want to make your home network more secure, the first step is to change the default wireless network name. This name is known as SSID.
Don’t use stimulus names. A name like “You Can’t Hack Me!” Often has the opposite effect. Because everyone with the least knowledge of hacking tends to hack this network.
The default name generally includes the router manufacturer and its model. Having this information makes the attack easier. Because each manufacturer’s routers have their own vulnerabilities. Make this information harder by changing the default name.
We suggest you not use names like “WiFi Ali” at all. You don’t want everybody to know which one belongs to you just by looking at the list of nearby networks.
Don’t forget this. Don’t use too much personal information in the chosen name of your network. Because you may be at risk of identity theft .
You can also hide the SSID in general in the router settings. Doing so will lose access to the network without knowing its name.
Step 2: Make sure you use strong and specific coding
You probably know that all wireless routers have a default username and password. This username and password are used to make the initial settings. The worst drawback is that if you don’t change these attributes, it’s hard to guess. Especially if the manufacturer is specified.
So be sure to change your default username and password as soon as possible.
A good password for a wireless network should contain at least 2 characters. Passwords must contain different numbers, letters, and symbols .
Step 4: Increase WiFi security by enabling network encryption
Wireless networks have different encryption. Like WEP, WPA and WPA2.
For better understanding of these names, for example, WPA2 stands for “WiFi Protected Access”. This concept is a security contract. WPA2 networks are everywhere, encrypting wireless network traffic. WPA replaces WEP and provides higher security. WPA2 was introduced after WPA and was replaced. Since Year 2, all certified wireless networks have been using WPA2.
Today, WPA2 AES is also a security standard, and all wireless networks are compatible with it. Make sure you enable WPA2 encryption in your router settings.
The good news is that WPA3 is about to become standardized and will soon replace WPA2. The WiFi Union has just introduced the next generation of wireless network security standards. The main purpose of this new standard is a common security problem: free wireless networks. In addition, there are other security enhancements. Including simplifying network security settings for users.
Step 2: Turn off the wireless router when not home
To increase the security of your home wireless network, we suggest turning off the router when not at home. We also recommend this when you are at home but do not need internet for a long time. For example, at night before bedtime you can turn off the router until morning.
By doing so, you block the way for hackers to access you when you are not at home, or do not need internet access.
Some of the benefits of disabling a wireless network include:
- – Security reasons: Turning off network equipment minimizes the chance of hackers attacking.
- – Increased security against power fluctuations: When you turn off network equipment, you reduce the chance of equipment being damaged by power fluctuations.
- – NR: Although new home routers have very little noise, but off them as little noise to remove and bring greater peace to your home.

Step 3: Where is your router located?
You probably haven’t thought about this yet. Where your Wi-Fi router is located can damage your network security.
Keep the wireless router as central as possible in the home . Why? The first is that it gives you equal access to the internet from anywhere in the house. The second reason is that you don’t want to get your network coverage out of the house. This will restrict other people’s access to your private network.
For these reasons, we recommend that you do not place a wireless router near the window. Because then there is nothing to stop the signals from leaving the house.
Step 3: Increase the security of your wireless network with a strong password for network administrator
To set up a wireless router you usually need access to a site or online platform. In this section you can make many changes to your network settings.
Most wireless routers have a default username and password. These default values are often something like “admin” and “password” or “admin” and “admin”. These values are easily guessable by hackers.
Did you know that the number of wireless networks has increased dramatically in the last five years? In year 2, the total number of wireless networks was 4 million . After 5 years, the total number of wireless networks has reached 3 million . Smartphones, laptops, and tablets have increased the number of wireless networks. Because of the high cost of mobile Internet packages, people often use wireless networks .
Step 2: Change the default IP of the wireless router
Changing the default IP router to another unusual IP is another step in increasing wireless network security. This will make your IP router’s guess difficult for the hacker.
To change the IP router, follow these steps:
- ۱. Enter the router settings at the administrator access level. Usually the default address of the router is one of these two addresses: 1.2.1.1 or 1.1.0.1
- ۲. When you enter the homepage, enter your username and password.
- ۳. From the Network section, select LAN.
- ۴. In the settings in this section, change the default IP address.
- ۵. Save the new settings.
Remember that you will need to enter a new IP from now on to enter the settings page.

Step 3: Disable DHCP functionality in the router settings
To increase the security of your wireless network, you must turn off the Dynamic Host Configuration (DHCP). DHCP’s task is to assign the IP to the devices connected to the network. Instead, you can assign a static IP to each device.
To do this, you must enter the IP address you want to connect to the network. Other IPs will not be able to connect to the network.
Step 2 Disable remote access
Most routers only allow network-connected devices to access settings. However, some routers have features that allow remote access to the settings.
When you turn off remote access, you get access to router settings from anyone not connected to the network .
To make this change, enter the router settings and look for the “Remote access” or “Remote administration” section.
Step 2: Always keep your router software up to date
Software is a vital part of maintaining network security. The wireless router firmware, like any other software, has security breaches that are fixed by the update. These security breaches provide a way for hackers to enter.
Unfortunately, many routers do not automatically update. So, you have to do it manually.
Even many routers that have auto-update capabilities do not enable this feature by default. You must find and enable this feature in the Settings section. But don’t forget! Firmware update is very important. Failure to do so will open the door for cybercriminals to enter your network.
Step 2: A firewall or firewall can help protect your wireless network
Firewalls are not always software, and they have some kind of hardware.
A hardware firewall does almost the same kind of software. But the main advantage of the hardware is the addition of an additional layer of security.
The good news is that high quality routers have an internal firewall. The firewall blocks any attacks. If your router has an internal firewall, we suggest you enable this feature.
Step 2: Increase the security of the devices that are most connected to your home network
Important: Don’t make any obvious vulnerabilities available to online criminals!
So far, you have dramatically increased the security of your router and home network. But make sure that no security breach will not be available online criminals.
Here are some ways we suggest you:
- – Remember to always keep your Internet connected devices up to date with the latest software available.
- – Apply all the latest security updates . This will ensure that security breaches are closed and not accessible to criminals.
- – Check for devices that are often connected to your home network. Make sure they all use the right antivirus software.
- – Make sure multilayer security layers protect your devices. Specialized security software such as up-to-date antivirus software and traffic control software.

The last word
Securing your home network should be a priority. A priority for everyone who cares about their information security. The items mentioned in this article are easily applicable by anyone.
Remember that your wireless network security can be poor. Weak network security will expose you to abuse. When cybercriminals can steal your WiFi information, just updating the software and a strong password is not enough.
We wrote this article to keep your home wireless network secure. Be sure to choose the right wireless router so you can adjust the settings. Because some routers still use WEP encryption and do not support these security methods. Then consider the tips provided when selecting a router.
]]>We see regular broadband companies need 50% growth each year. The growing need for more bandwidth is coupled with more job opportunities,
Experts from Wavestone’s Smart Networks Subject Matter are regularly reviewing new and up-to-date technologies to provide good analysis of the trends that will dominate the networking world.
Here’s a look at the top five trends in the networking world that are going to have a huge impact on the world of networking jobs, as well as the top five networking jobs in the field of data centers.
Deploying Next Generation Networks – SD WAN
The main trend towards using newer SD-WAN technologies to deliver flexible network infrastructure including CPE and VNF support is increasing. Large-scale software-based networks increase network speed and security and reduce costs and complexity in parallel.
The SD-WAN software-based approach enables organizations to take a hybrid approach to their network infrastructure and achieve high efficiency not only in traditional MPLS but also in the application of other communication technologies such as 4G and LTE.
We are seeing that most organizations are looking to deploy such networks in their own infrastructure, and we expect the deployment process to be implemented in most organizations by 2020.
The benefits of these networks include providing software services, prioritizing and allocating traffic to the network that reduces software performance and delays staff performance, replacing smart software with expensive hardware to reduce costs and centralized management.
Decentralization
Traditional architectures direct all traffic to the data center, providing security and access to information over the Internet. Increasing cloud usage and greater collaboration with partners and providers has challenged the model.
The trend that has been widespread for many years is the emergence of cloud-based security services and the direct connection to cloud-based technologies,
which has led many organizations to move to a cloud-based infrastructure to move away from a centralized approach to optimizing their communications.
This approach is recognized by many as a top model in most organizations, and even large corporations are turning to Microsoft, Amazon and Google’s cloud-based services.
The growing growth of a broad supply chain ecosystem
Large organizations will move away from a single supplier approach due to their business needs and will seek to interact with different suppliers.
This approach leads to the development of more advanced models called Service Integration and Service Layer (SIAM). In this mechanism, services are integrated internally, either through an IT coordinator complex or through a network service provider or telecommunications operator.
In addition, in order to optimize prices and improve efficiency, engagement with individual or regional technology providers is enhanced.
These individual technology providers are the same companies we refer to as contractors. Companies that do some of the work for larger companies. Google and Microsoft are good examples of different contractors working on this model.
Wireless networking first and foremost
Improved wireless technology, management and security of these networks have led many organizations to deploy wireless networks as a first step. Wireless networks reduce the costs associated with adding, relocating and changing the wired LAN (LAN) infrastructure and improving network reliability.
In this cloud-based mechanism, cloud services will be introduced into organizations in a wider fashion, along with advanced monitoring services and tools.
Expect 802.11ax-based solutions that are four times more capable to be deployed across devices next year. A solution that enhances job opportunities associated with wireless networks.

The fifth generation of communication networks
2019 saw the emergence of 5G (5G) services. A network that has the potential to increase the operating capacity of today’s networks by 10 times the current capacity and is able to provide different service models to suppliers.
We expect many large organizations and operators in 2020 to seek to replace or enhance fixed network connections and to look more seriously at deploying large-scale IoT solutions.
Such a mechanism requires a robust, high-speed communication network such as 5G, and more importantly for those who know what 5G is, how to use it, and how to fix it.
It is clear that technology and communications are advancing rapidly. It is important for organizations to determine which of these new technologies is right for their business and how these technologies will help them improve efficiency and increase profits.
With a simple glance at the list above, you will find that the 5 main trends each create a very broad set of job opportunities. Finally, let’s take a look at five important data center business trends.
In the world of a data center, five trends tend to be well below pay.
1. Data Center Project Manager :
Organizations need a specialized workforce to oversee the design and construction of data centers.
A person who has a good understanding of needs and can predict the future needs of the project. These people are mainly employed in large organizations that are going to implement data centers in different cities and regions.
These include banks, financial institutions, large-scale national producers, and telecommunications operators. The average salary for this job ranges from $ 86,000 to $ 115,000 a year.
2. Compliance Officer :
A person who knows the legal requirements, is familiar with the internal and external laws and policies associated with the data center and assures the organization that no breach has occurred.
The obligations and job descriptions of contractors are burdensome, as they must ensure that the design of offshore projects complies with current laws and at the same time does not conflict with internal laws.
Given the enactment of various IT-related laws in different countries that make data monitoring and management difficult, almost all large organizations need such a person, as teams in the process of building a data center may not pay attention to international law that may eventually result in penalties.
Brings heavy to an organization. The average salary for this job ranges from $ 69,000 to $ 104,000 a year.
3. Cybersecurity Specialist :
Cyber security jobs are always needed. In relation to data centers, cyber security means protecting network equipment against various types of physical, virtual, internal and external attacks.
As you can see, the responsibility of a cyber security expert is very heavy, on the one hand, to make sure that regular employees do not have access to the racks and servers, that the data center cooling equipment does not have security problems or vulnerabilities, patches and updates are regularly installed in the firmware.
However, security personnel cannot access the equipment through the internal network and, more importantly, security mechanisms are properly configured. The average salary for this job ranges from $ 122,000 to $ 155,000 a year.
4. Data Center Technician :
Data center technicians are a degree lower than a network expert and are among the first group of people to be in contact with the data center after it is completed.
They are graduates of computer science and have specialized management and data center courses. These people are hired to solve problems in the data center.
A data center technician makes sure that the network status is stable and also reduces the costs of the organization because in some cases organizations are hiring a network technician rather than hiring a network manager or expert. The average salary for this job ranges from $ 37,000 to $ 46,000 a year.
5. Cloud Architect :
As noted, virtual and cloud-based technologies are becoming increasingly popular, and these technologies are expected to be increasingly welcomed by Iranian users and organizations.
Designing a hybrid or cloud-based infrastructure Cloud needs a cloud architect Because cloud services are mainly moving to the public cloud and private clouds will gradually be marginalized,
the cloud architect should be able to properly balance the use of public and private cloud services Cloud computing architecture of fragmented layers Fi namely Layer Infrastructure,
Virtual Infrastructure Layer, Cloud Management, Consumer Layer, Support and Operations Management Layer (OSS), Business Support Layer ( BSS), Security layer, Resiliency layer and Consumability layer are built in.
As you can see, proper implementation of these layers requires a high level of expertise. The average salary for this job ranges from $ 114,000 to $ 142,000 per year.
Today, despite all the advances in wireless (wireless) technology, many computer networks still use their cables to transmit their data.
Twisted pair cable:
Twisted-pair network cables are used to transfer data to network systems. History of twisted cables (TP) goes back to 1970 and the time of the invention of the telephone. This type of cable has played an important and influential role in the history of human communication.
Twisted-pair network cable consist of a number of twisted-pair pairs with spiral insulation. The most prestigious brands in this field are Legrand Network Cable, Nansense Network Cable, Schneider Network Cable, Balden Network Cable and more.
Commonly used network cables today consist of two or four pairs of twisted wires. In the 1990s, these cables were recognized as the standard for Ethernet cabling and were initially used as CAT3 cables at speeds of 10 Mbps.
Subsequently, improved versions of the CAT5 and CAT5e cables were able to increase the data transfer rate by up to 1000 Mbps. Today, improved versions of network cables include CAT6, CAT6A, CAT7 and CAT8.
The letter A stands for Augmented meaning completed. The reason for using this name in some types of network cable is the greater bandwidth of that cable.
The twisted-pair network cables are divided into two categories: Shieldless and Foil (UTP) and Shielded and Foil (SFTP). However, more fuel-efficient models are also available in the market with the names FTP (foil-free shield) and STP (foil-free shield).
UTP cables include twisted pair with a plastic layer and are more widely used in Ethernet networks because of their lower cost. UTP cables are categorized into different types depending on the thickness of the wires used and the quality of data transmission on them, with the CAT letters of the word Category meaning to name these cables.
CAT1 cables are mainly used for voice transmission at a maximum speed of 1 Mbps and CAT2 cables for voice and data transmission at a maximum speed of 4 Mbps. CAT3 cables are used to transmit data at a maximum speed of 10 Mbps.
CAT5 cables are used to transmit data at a speed of up to 150 Mbps. There is, of course, some fifth-class cables that are used to transmit data at up to gigabits per second (1000 Mbps) and are called CAT5e cables.
The letter e is derived from the word Enhanced in the sense of improved. CAT6 cables also have a transmission speed of 1000 Mbps and CAT6A cables have a transmission speed of 10,000 Mbps.
CAT5e and CAT6 cables are nowadays regarded as the most widely used cables in the network domain. CAT7 cables are only used for shielded cables and support high-speed transmission up to 10,000 Mbps.
CAT8 cables are now available in the market today with amazing speeds and unparalleled 2 GHz bandwidth.
Laminated cables (SFTPs), like UTP cables, are made of twisted copper wire with an aluminum foil cladding, which prevents electromagnetic interference but in turn lowers the cost of the cable.
It also increases. Remarkably, in the case of network cables, the coatings on these conductors are twisted.
Most of these cables are PVC laminated but sometimes LSZH lined cables are also available in the market. The abbreviated LSZH for Low Smoke Zero Halogen means halogen-free cables.
That is, these types of cables do not produce toxic smoke when burning.
The older generation network cables with RJ45 socket and CAT7 and CAT8 network cables with GG45 socket are connected to other network equipment. The most important and most used of these equipment are patch panels and patch cords .
The network patch panel has different ports and as a switch, it is widely used in network systems. The network patch, or LAN cable, also has different sockets with two sockets that can be used to connect different systems to the network.
UTP and SFTP network cables are widely used today because of their high transmission speed,
good long-distance data quality, relatively low cost and easy cabling.
Outdoor network cables are also used when network cabling needs to be done in the open.
By default, when setting the IPv6 address, Windows 10 generates a random number to fill in the bits required for the IPv6 address card segment.
This is part of a series of Networking Plus tutorials previously published on the network site.
Click here to view the list and buy the Book + Network Guide to Networks.
Change Ipv6 auto configuration settings (especially for people with access to the Ipv6 protocol)
1. Open the command prompt window.
2. Type the ipconfig / all command and press the Inter key. What is the current IPv6 address of the computer and the MAC address? (Compare these two addresses carefully. Are these numbers interconnected or unrelated?)
3. To disable the ability to generate a random IP address, enter the command:
netsh interface ipv6 set global
randomizeidentifiers = disabled
4. To help Windows use the standard EUI-64 instead of the default settings as follows:
netsh interface ipv6 set privacy
state = disabled
The following figure shows where to enter both the commands and the output of these commands.

5. Re-enter the ipconfig / all command What is your computer’s new IPv6 address? How similar is the new address to the MAC address?
Note the second part of the IPv6 address after FE80 :: that has a constant value of FF FE used to construct this part of the values in the MAC address. The IPv6 address host may use slightly different OUIs on the MAC address, as the seventh bit of the MAC address is reversed.
6. Repeat the random IPv6 address using the following two commands.
netsh interface ipv6 set global
randomizeidentifiers = enabled
netsh interface ipv6 set privacy
state = enabled
From audible devices like Apple’s Powerbeats Pro to ThirdEye’s X2 Augmented Reality Glasses, it should be acknowledged that the hottest wearable of 2019 include a range of applications and methods that show how technology can be added to humans. You read 9 of the hottest wearable devices in 2019.
2019 was a great year for wearables . The number of devices marketed reached a new record in the third quarter of 2019 . As IDC reports, sales of wearables rose by a stunning 94.6 percent to 84.5 million worldwide.
The explosion in the wearables market is largely due to the unprecedented popularity of hearing aids like the Apple AirPad. This new category of wearable technology accounts for half of the market in the third quarter of last year. After that, bracelets and smart watches are second and third.
Here are 9 of the hottest wearables of 2019 from Apple’s Powerbeats Pro to ThirdEye X2 Augmented Reality Glasses.
The best and hottest wearable devices of 2019
1- Apple Powerbeats Pro

The Apple Powerbeats Pro wearable made by Apple’s Bates brand is a high-end pair of airbags that deliver power and sound to the user. In terms of voice assistant, the headphones are integrated with Apple Siri and the user can say “Hey Siri” to activate this voice assistant without having to touch his iPhone. The airbags automatically detect coming out of the ear and stop playing music until they get back into the ear. The retail price of this wearable is $ 249.95.
2- Apple Watch Series 5

The latest smart watch Apple introduced is the Apple Watch Series 5. In this model, optimizations are made over the previous generation, such as the introduction of the ever-bright Retina capability without draining the battery. Other features include a compass for better navigation, an international SOS for emergencies, and the use of ceramics and titanium for a more elegant design. This wearable is available for $ 399.
3- Elvie Pump

Wearable Elvie Pump is the first silent wearable pump with no pipes or wires. This machine is made up of 5 parts and assembly and cleaning is very simple. The retail price of this wearable device is $ 279.
4- Form Swim Goggles

The Form Swim Goggles wearable comes with an augmented reality display that provides swimmers different metrics. In addition, Form has recently launched a collaboration with Polar, which manufactures these glasses, and monitors the heart rate of the swimmer’s OH1 and + OH1 monitors by connecting to the strap. Form Swim Goggles glasses are priced at $ 199 with Bluetooth connectivity and 16 hours of battery life.
5- Fitbit Inspire HR

Fitbit’s Inspire HR wearable is a fitness tracker that constantly monitors heart rate to help users maximize their workout sessions, identify sleep patterns, and track calorie burning. This waterproof device can also monitor hearing, walking, running and cycling. The Fitbit Inspire HR is priced at $ 100.
6- Matrix PowerWatch 2

The new Matrix Industries smartwatch is a PoweWatch 2 model that uses solar cells and human heat to charge it. This means you do not need to plug it into the power supply. Compared to its predecessor, the new color display adds GPS connectivity as well as a heart rate monitor. It’s priced at $ 499.
7- Nubia Alpha

The Nubia Alpha smart watch has a flexible 4-inch folding OLED display that wraps around the wrist. Users can control the watch’s operating system by waving their hands to the operating system. Fitness and health monitoring, Bluetooth calling and SMS instant reminders are another $ 299.
8- Stryd

The Stryd is a wearable design to help runners optimize their pressure levels using a variety of sensors built-in for movement, temperature and humidity. The wearable wraps around the runner’s shoes and can detect the winds that hit the front or back and provide a feedback to the runner. Other features of the Stryd include speed tracking, running and fatigue. This wearable is available for $ 219.
9- ThirdEye X2 Smart Glasses

ThirdEye calls the X2 the world’s smallest integrated reality glasses. This title is due to its small size, lightness and its slim display. It has a 42-degree viewing angle and features an HD display with a resolution of 1280×720. Other features include CPU / GPU with 3 GB of RAM and 32 GB of storage. X2 smart glasses are available for $ 1950.
When you collect network data with Wireshark based on the default settings, it also collects information about the network card manufacturer, allowing you to obtain information about each device.
This is part of a series of Networking Plus tutorials previously published on the network site.
Click here to view the list and buy the Book + Network Guide to Networks.
Wireshark is a free network open source analytics tool that helps network experts identify network messaging and implement an OSI-based model. Most packets sent over a network have the recipient’s MAC address, the sender, or both.
When you collect network data with Wireshark based on the default settings, it also collects information about the network card manufacturer, allowing you to obtain information about each device.
When you download and run the tool above you will see an image like the one below.

In the figure above, just click on your Active Connection (WiFi or Wired) in the above image to see MacAddress.
Clicking on this will bring up a window that shows the activities done on the network.
The middle panel of this window shows information about the status of communications and the protocols used. In this panel, if you double-click on the Ethernet II option to open it, Wireshark will show your Mac adresses the network card in front of the Source field as shown below.

Occasionally, you have to work with physical addresses provided by an output command or access information beyond what Wireshark offers.
In such cases, it is advisable to use online MAC address tables similar to Wireshark’s OUI Lookup Tool.
1. You can see in the figure above that the MAC address is specified in the source field. The first three bytes of this address, c8: f7: 33, specify the device’s OUI. If you go to wireshark.org/tools/oui-lookup, enter these values into the OUI search field, and click the Find button, the Wireshark OUI Lookup tool will give you some interesting information.
Access Macadress information via command line
2. To view Macadress information via the command line, open the Command Prompt window
and enter the ipconfig / all command to identify the physical address of the network card.
3. To select and copy the required information to the clipboard, first press Ctrl + M to enable markup,
then select the first three bytes of the physical address of the active network connection
with the mouse and press Ctrl + C. (In the Command Prompt window, copy the first three bytes of MacAddress.)
4. Navigate to the Wireshark website search field (as you mentioned in the previous paragraph) and press Ctrl + V to place the information into the Wireshark Lookup Tool field, then click Find. What company is your network card manufacturer?
The IP address or address can be fixed (static) or variable (dynamic). The differences between static IPs and dynamic IPs and their advantages and disadvantages have led to different applications in each.
What is the Internet Protocol or IP Address?
An Internet Protocol (IP address) is a unique identifier that assigns to each computer and equipment connected to the Internet (and other Internet Protocol based networks) and identifies their digital identity. An IP address is a quadrilateral number that is separated by a segment from each other (eg: 192.168.1.1). Using an IP address can detect a computer from another computer on the Internet and even get their geographical location and the company that hosts them. The IP address is either fixed (static) or variable (dynamic).
What is a Dynamic IP Address?
Most Internet-connected devices have a dynamic or dynamic IP address. Your IPS, the company you receive from the Internet, can always change the dynamic IP addresses so that each time you connect to the Internet, your computer’s IP address is different from the address assigned to it, although this is not always the case.
It doesn’t happen, and for many times the variable IP can stay the same for weeks, months, and even years and won’t change. Home users usually don’t notice the IP address change. Changing the dynamic or dynamic address does not affect users’ browsing and day-to-day operations.
Unless you have a specific configuration for your IP, you won’t even notice the difference between a static (static) IP and a variable (dynamic) IP. Since variable IP is cheaper than fixed IP, most home users use variable IP.
Benefits of Variable IP (Dynamic)
- Dynamic IPs are less expensive and more economical.
- Variable IPs require less care than fixed IPs.
- Variable IPs face fewer security threats.
Disadvantages of Variable IP (Dynamic)
- Dynamic IPs often have more downtime.
- If your IP is variable, your GPS-based services (GPS, etc.) may not be able to pinpoint the exact location of your business (for example, the exact location of your company on online maps).
- Remote access to variable IPs is usually more insecure.
What is a Static IP Address?
A static or static IP address is always fix and will not change. Even turning off the computer or restarting the network router (router) does not change the device’s fixed IP. To get a static IP address, you need to pay extra for your IPS to reserve any number of IPs from the IP repository. The IPs that are reserved for you only apply to your computers and systems. Billions of addresses that have not yet been reserved are used as variable or dynamic IPs.
Which businesses usually use static IP?
Home users usually do not need a fixed IP address. But some large collections may require a static or static IP address to facilitate their work, for example:
- File Transfer Protocol Servers (FTP server)
- Email servers
- VPN servers
- Hosting services
Many of these businesses, and similar ones, register their fixed IPs for security considerations in a whitelist so that IPs can be assign to authorize users.
Benefits of static (static) IP
- A static IP address will never change, even if the device reboots.
- Fixed IP addresses are suitable for businesses that rely on IP addresses.
- If your IP is fix, geography-base services will find the exact location of your business much easier.
- Fixed IP usually has less downtime.
Disadvantages of Fixed (Static) IP
- Fixed (static) IPs are more susceptible to security breaches because hackers have the opportunity to attack a network with a fixed IP.
- Fixed IP addresses are more expensive.
Businesses can compensate for weak IP addresses by creating powerful firewalls (firewalls) and using VPNs to transact data, as well as by securing and updating cloud database services and paying more to secure their websites. Although none of the above security methods and tools are perfect, when used together, they are usually efficient enough to withstand hacking and blackmail attacks and protect online assets.
What is a Better IP Fix IP?
Given the advantages and disadvantages of both types of IP addresses, it is recommend to use a fixed IP:
- If the company or organization has servers and websites that must be running at least 99.99% of the year (their time is almost zero)
- If using VoIP or other digital voice servers in the mechanisms
- And If employees need remote access to perform their duties from home or open networks,
And If none of the aforemention technologies are use and will not work in the near future, changing the IP address is a more cost-effective choice.
Detecting a static (static) IP address from a variable (dynamic) IP address
Any computer, no matter what its operating system, can get a fixed or variable IP. For example, to find out what kind of IP your current Windows computer is:
Find the type of IP address in Windows
- Open the Windows Command Prompt program.
- Type ipconfig / all.
- Find the DHCP Enabled expression.
- If the word yes is write in front of DHCP Enable, your IP address will change. If the word no is written, your IP is fixed.
Can I switch from a fixed IP to a variable IP?
Currently, almost all ISPs dynamically assign IP addresses to their clients. The main reason is the lack of IPs. When addressing is dynamic, IPS is less restrictive because it can distribute different IPs to its users. If your business needs a fixed IP, you should talk to your IPS, because you can’t get a fixed IP elsewhere. But even if your IP is variable, you can still get some of the benefits of a fixed IP using dynamic DNS services.
Connecting to an open WiFi Network such as a free wireless hotspot, exposes your computer or mobile device to security risks.
To increase the security level on your computer, phone or tablet, you need to check your device’s wireless network settings to see if these settings are enabled. Automatic connection to WiFi should only be used in temporary conditions.
Forgetting wifi networks
Another thing to keep in mind about open networks is that your device may be configure to remember the connections you’ve used in the past, whether it’s open or private. And be personal. Network information storage is a feature that makes you no longer have to enter related information every time you connect to a network.
But if you want to have complete control over the networks you connect to, you must forget about the networks. Most devices provide you with an option to delete a connection profile.
How to disable automatic connection to a WiFi network
In Windows
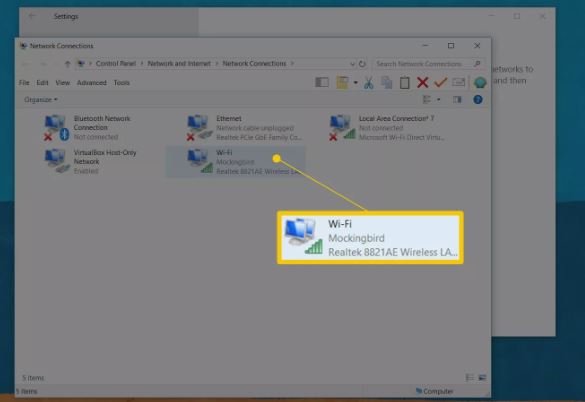
Step 1 In Windows 10, click on the Action Center icon in the lower right corner of the screen and select All Settings.
Step 2 Now select Network & Internet in the Windows Settings section.
The Step 3. Select Wi-Fi from the options on the left and then in the panel
on the bottom right of the Related Settings section,
select Change Adapter Options to open the Network Connections window.
Step 4. Double-click (or right-click and select Properties) the Wi-Fi connection for your network to open the Wi-Fi Status window.
Step 5. In the General tab, click the Wireless Properties button to open the Wireless Network Properties page. Then on this page under the Connection tab, uncheck Connect Automatically When This Network is in Range to disable it.
On iOS
On both iPhone and iPad devices, there is an option for each Wi-Fi profile call Auto-Join,
which automatically connects when your device is within range of this network.
To prevent this from happening, go to Settings> Wi-Fi and tap the small i icon next to the network name to find the Auto-Join button. Disable it to stop automatic connection to this network.
WiFi Network On Android
To stop Android devices from connecting to open networks, go to your phone’s Settings section and select Network & Internet> Wi-Fi> Wi-Fi preferences. Then set the Connect to open networks option button to Off.